GSM Technology
April 10, 2007 – 7:37 am
GSM

Definition
[[GSM]] is an acronym for Global System for Mobile communication (derived from Groupe Spécial Mobile) which is the most widely accepted standard for digital cellular communications. Even though the idea of a cell based radio communication system originated at the Bell Labs in the early 1970s the idea was not implemented until mobile communication systems experienced a rapid growth in Europe, particularly in UK and Scandinavia. In the early 1980′s when the initial growth of cellular phones was just starting in Europe, a need was felt to have a uniform standard for mobile phones that would equipment and technology being developed could be used in different regions. To overcome the problems posed by the rapid growth of mobile phones, the Groupe Spacial Mobile (GSM) was formed by the Conference of European Posts and Telecommunications (CEPT). The GSM had to meet the following criteria:
Spectrum
Smooth international roaming
Cheaper mobile phones
Enhanced voice quality
Compatible with ISDN(Integrated Services Digital Network) and other systems
Ability to provide new services
CEPT passed the responsibility for the GSM specifications in 1989 to European Telecommunications Standards Institute (ETSI). GSM’s main aim is to describe the functionality and the interface for each component of the system and to give guidance on the design of the system. Even though the phase I of the GSM specifications were published in 1990 the commercial use of GSM didn’t start until 1991.
The most important events in the development of the GSM system are presented in the following table.
|
Year |
Events |
| 1982 | CEPT establishes a GSM group in order to develop the standards for a pan-European cellular mobile system |
| 1985 | Adoption of a list of recommendations to be generated by the group |
| 1986 | Field tests were performed in order to test the different radio techniques proposed for the air interface |
| 1987 | TDMA is chosen as access method (in fact, it will be used with FDMA) Initial Memorandum of Understanding (MoU) signed by telecommunication operators (representing 12 countries) |
| 1988 | Validation of the GSM system |
| 1989 | The responsibility of the GSM specifications is passed to the ETSI |
| 1990 | Appearance of the phase 1 of the GSM specifications |
| 1991 | Commercial launch of the GSM service |
| 1992 | Enlargement of the countries that signed the GSM- MoU> Coverage of larger cities/airports |
| 1993 |
Coverage of main roads GSM services start outside Europe |
| 1995 | Phase 2 of the GSM specifications Coverage of rural areas |
Today GSM is not just a European standard; GSM networks are operational in more than 80 countries around the world. The number of GSM subscribers is increasing at an exponential rate.
Advantages of digital system
Before the advent of GSM most of the cellular systems were analog. The GSM was the first digital cellular system. As the new number of subscribers was increasing in an exponential way, the analog technology prevalent at that time was finding it difficult to cope up with the increasing demand. The new analog technology to handle the increases traffic was very expensive and the digital radio was more cost effective. By using the digital system, different communication systems such as ISDN could be made compatible to each other. Also it is much easier to modify the characteristics of a digital system than that of an analog system. The quality of service (QoS), which is a very important parameter in deciding the quality of a network, is much more in a digital system than in an analog system. In digital system fadeouts, crosstalk etc are reduced by converting the analog signal into bits. Also, various digital coding methods can be employed in digital systems to improve the quality of service.
Cellular systems
The cellular structure
The area in a cellular system is divided into cells. Each cell has is covered by one transmitter (though sometimes a number of small transmitters may be used). The transmitter’s power determines the size of a cell.
The frequency bandwidth allotted to a cellular system is not limited to a particular cell but spread over a group of cells. This distribution is repeated over a group of cells in the covering area of an operator. By this way frequencies used in a cell can be reused in another cell at an appreciable distance away. The distance between two cells using same frequency should be such that there is no interference. The frequency reuse helps in increasing the capacity of the system. To enable efficient reuse of frequencies low power transmitters are used as then the signal propagates only to a limited area.
In order to work properly, a cellular system must meet the following two conditions:
The power level of a transmitter within a single cell must be limited to reduce the interference with the transmitters of neighboring cells. The interference will not produce any damage to the system if a distance of about 2.5 to 3 times the diameter of a cell is maintained between transmitters.
Adjacent cells can not share the same channel. To reduce the interference, the frequencies must be reused only within a certain pattern.
In order to exchange the information needed to maintain the communication links within the cellular network, several radio channels are reserved for the signaling information.
Cluster
The cells are grouped together as clusters. The number of cells in a cluster must be determined so that the cluster can be repeated continuously within the covering area of an operator. The typical clusters contain 4, 7, 12 or 21 cells. The number of cells in each cluster is very important. The smaller the number of cells per cluster is, the bigger the number of channels per cell will be. The capacity of each cell will be therefore increased. However a balance must be found in order to avoid the interference that could occur between neighboring clusters. This interference is produced by the small size of the clusters (the size of the cluster is defined by the number of cells per cluster). The total number of channels per cell depends on the number of available channels and the type of cluster used.
Types of cells
The density of population in a country is so varied that different types of cells are used:
Macrocells
Microcells
Selective cells
Umbrella cells
Macrocells: The macrocells are large cells for remote and sparsely populated areas.
Microcells: These cells are used for densely populated areas like big cities. By splitting the existing areas into smaller cells, the number of channels available is increased as well as the capacity of the cells. The power level of the transmitters used in these cells is then decreased, reducing the possibility of interference between neighboring cells.
Selective cells: It is not always useful to define a cell with a full coverage of 360 degrees. In some cases, cells with a particular shape and coverage are needed. These cells are called selective cells. Typical examples of selective cells are the cells that may be located at the entrances of tunnels where coverage of 360 degrees is not needed. In this case, a selective cell with coverage of 120 degrees is used.
Umbrella cells: A freeway crossing very small cells produces a large number of handovers among the different small neighboring cells. In order to solve this problem, the concept of umbrella cells is introduced. An umbrella cell covers several microcells. The power level inside an umbrella cell is increased compared to the power levels used in the microcells that form the umbrella cell. When the speed of the cell phones is too high, the mobile is handed off to the umbrella cell. The mobile will then stay in the same cell for longer duration (in this case the umbrella cell). This will reduce the number of handovers and the work of the network.
The GSM network
Architecture of the GSM network
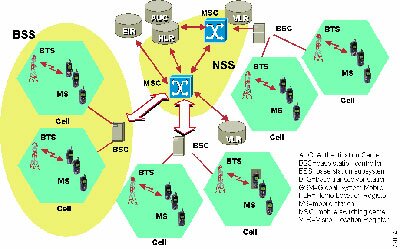
The GSM technical specifications define the different entities that form the GSM network by defining their functions and interface requirements.
The GSM network can be divided into four main parts:
The Mobile Station (MS).
The Base Station Subsystem (BSS).
The Network and Switching Subsystem (NSS).
The Operation and Support Subsystem (OSS).
The architecture of the GSM network is presented in figure 1.
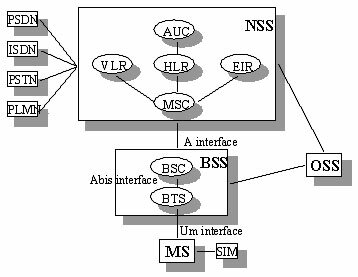
Figure 1: Architecture of the GSM network
Mobile Station
A Mobile Station consists of two main elements:
The mobile equipment or terminal.
The Subscriber Identity Module (SIM).
The Terminal
There are different types of terminals distinguished principally by their power and application:
The fixed terminals are the ones installed in cars. Their maximum allowed output power is 20 W.
The GSM portable terminals can also be installed in vehicles. Their maximum allowed output power is 8W.
The handheld terminals have experienced most success because they are light and small. These terminals emit up to 2 W.
The SIM
The SIM is a smart card that identifies the terminal. By inserting the SIM card into the terminal, the user can have access to all the subscribed services. Without the SIM card, the terminal is not operational.
The SIM card is protected by a four-digit Personal Identification Number (PIN). In order to identify the subscriber to the system, the SIM card contains some parameters of the user such as its International Mobile Subscriber Identity (IMSI).
Another advantage of the SIM card is the mobility of the users. In fact, the only element that personalizes a terminal is the SIM card. Therefore, the user can have access to its subscribed services in any terminal using its SIM card.
The Base Station Subsystem
The BSS connects the Mobile Station and the NSS. It is in charge of the transmission and reception. The BSS can be divided into two parts:
The Base Transceiver Station (BTS) or Base Station.
The Base Station Controller (BSC).
The Base Transceiver Station
The BTS corresponds to the transceivers and antennas used in each cell of the network. A BTS is usually placed in the center of a cell. Its transmitting power defines the size of a cell. Each BTS has between one and sixteen transceivers depending on the density of users in the cell.
The Base Station Controller
The BSC controls a group of BTS and manages their radio resources. A BSC is principally in charge of handovers, frequency hopping, exchange functions and control of the radio frequency power levels of the BTSs.
The Network and Switching Subsystem
Its main role is to manage the communications between the mobile users and other users, such as mobile users, ISDN users, fixed telephony users, etc. It also includes data bases needed in order to store information about the subscribers and to manage their mobility. The different components of the NSS are described below.
The Mobile services Switching Center (MSC)
It is the central component of the NSS. The MSC performs the switching functions of the network. It also provides connection to other networks.
The Gateway Mobile services Switching Center (GMSC)
A gateway is a node interconnecting two networks. The GMSC is the interface between the mobile cellular network and the PSTN. It is in charge of routing calls from the fixed network towards a GSM user. The GMSC is often implemented in the same machines as the MSC.
Home Location Register (HLR)
The HLR is considered as a very important database that stores information of the subscribers belonging to the covering area of a MSC. It also stores the current location of these subscribers and the services to which they have access. The location of the subscriber corresponds to the SS7 address of the Visitor Location Register (VLR) associated to the terminal.
Â
Visitor Location Register (VLR)
The VLR contains information from a subscriber’s HLR necessary in order to provide the subscribed services to visiting users. When a subscriber enters the covering area of a new MSC, the VLR associated to this MSC will request information about the new subscriber to its corresponding HLR. The VLR will then have enough information in order to assure the subscribed services without needing to ask the HLR each time a communication is established.
The VLR is always implemented together with a MSC; so the area under control of the MSC is also the area under control of the VLR.
The Authentication Center (AuC)
The AuC register is used for security purposes. It provides the parameters needed for authentication and encryption functions. These parameters help to verify the user’s identity.
The Equipment Identity Register (EIR)
The EIR is also used for security purposes. It is a register containing information about the mobile equipments. More particularly, it contains a list of all valid terminals. A terminal is identified by its International Mobile Equipment Identity (IMEI). The EIR allows then to forbid calls from stolen or unauthorized terminals (e.g., a terminal which does not respect the specifications concerning the output RF power).
The GSM Interworking Unit (GIWU)
The GIWU corresponds to an interface to various networks for data communications. During these communications, the transmission of speech and data can be alternated.
The Operation and Support Subsystem (OSS)
The OSS is connected to the different components of the NSS and to the BSC, in order to control and monitor the GSM system. It is also in charge of controlling the traffic load of the BSS.
However, the increasing number of base stations, due to the development of cellular radio networks, has forced that some of the maintenance tasks are transferred to the BTS. This transfer decreases considerably the costs of the maintenance of the system.
 The GSM functions
In GSM, five main functions can be defined:
Transmission.
Radio Resources management (RR).
Mobility Management (MM).
Communication Management (CM).
Operation, Administration and Maintenance (OAM).
Transmission
The transmission function includes two sub-functions:
The first one is related to the means needed for the transmission of user information.
The second one is related to the means needed for the transmission of signaling information.
Not all the components of the GSM network are strongly related with the transmission functions. The MS, the BTS and the BSC, among others, are deeply concerned with transmission. But other components, such as the registers HLR, VLR or EIR, are only concerned with the transmission for their signaling needs with other components of the GSM network.
Radio Resources management (RR)
The role of the RR function is to establish, maintain and release communication links between mobile stations and the MSC. The elements that are mainly concerned with the RR function are the mobile station and the base station. However, as the RR function is also in charge of maintaining a connection even if the user moves from one cell to another, the MSC, in charge of handovers, is also concerned with the RR functions.
The RR is also responsible for the management of the frequency spectrum and the reaction of the network to changing radio environment conditions. Some of the main RR procedures that assure its responsibilities are:
Channel assignment, change and release.
Handover.
Frequency hopping.
Power-level control.
Discontinuous transmission and reception.
Timing advance.
Handover
The user movements can produce the need to change the channel or cell, especially when the quality of the communication is decreasing. This procedure of changing the resources is called handover. Four different types of handovers can be distinguished:
Handover of channels in the same cell.
Handover of cells controlled by the same BSC.
Handover of cells belonging to the same MSC but controlled by different BSCs.
Handover of cells controlled by different MSCs.
Handovers are mainly controlled by the MSC. However in order to avoid unnecessary signaling information, the first two types of handovers are managed by the concerned BSC (in this case, the MSC is only notified of the handover). The mobile station is the active participant in this procedure. In order to perform the handover, the mobile station controls continuously its own signal strength and the signal strength of the neighboring cells. The list of cells that must be monitored by the mobile station is given by the base station. The power measurements allow deciding which the best cell is in order to maintain the quality of the communication link.
Frequency hopping
The propagation conditions and therefore the multipath fading depend on the radio frequency. In order to avoid important differences in the quality of the channels, the slow frequency hopping is introduced. The slow frequency hopping changes the frequency with every TDMA frame. A fast frequency hopping changes the frequency many times per frame but it is not used in GSM. The frequency hopping also reduces the effects of co-channel interference.
There are different types of frequency hopping algorithms. The algorithm selected is sent through the Broadcast Control Channels.
Even if frequency hopping can be very useful for the system, a base station does not have to support it necessarily. On the other hand, a mobile station has to accept frequency hopping when a base station decides to use it.
Power level control
At the same time the base stations perform the timing measurements, they also perform measurements on the power level of the different mobile stations. These power levels are adjusted so that the power is nearly the same for each burst.
A base station also controls its power level. The mobile station measures the strength and the quality of the signal between itself and the base station. If the mobile station does not receive correctly the signal, the base station changes its power level
Discontinuous Transmission and Reception
Discontinuous Transmission (DTX):
The function of the DTX is to suspend the radio transmission during the silence periods. This is very significant if the fact that a person speaks less than 40 or 50 percent during a conversation is taken into consideration. The DTX helps then to reduce interference between different cells and to increase the capacity of the system. It also extends the life of a mobile’s battery. The DTX function is performed thanks to two main features:
The Voice Activity Detection (VAD), which has to determine whether the sound represents speech or noise, even if the background noise is very important. If the voice signal is considered as noise, the transmitter is turned off producing then, an unpleasant effect called clipping.
The comfort noise. An inconvenient of the DTX function is that when the signal is considered as noise, the transmitter is turned off and therefore, a total silence is heard at the receiver. This can be very annoying to the user at the reception because it seems that the connection is dead. In order to overcome this problem, the receiver creates a minimum of background noise called comfort noise. The comfort noise eliminates the impression that the connection is dead.
Discontinuous Reception
It is a method used to conserve the mobile station’s power. The paging channel is divided into sub channels corresponding to single mobile stations. Each mobile station will then only ‘listen’ to its sub channel and will stay in the sleep mode during the other sub channels of the paging channel.
Mobility Management
The MM function is in charge of all the aspects related with the mobility of the user, specially the location management and the authentication and security.
Location management
When a mobile station is powered on, it performs a location update procedure by indicating its IMSI to the network. The first location update procedure is called the IMSI attach procedure.
The mobile station also performs location updating, in order to indicate its current location, when it moves to a new Location Area or a different PLMN. This location updating message is sent to the new MSC/VLR, which gives the location information to the subscriber’s HLR. If the mobile station is authorized in the new MSC/VLR, the subscriber’s HLR cancels the registration of the mobile station with the old MSC/VLR.
A location updating is also performed periodically. If after the updating time period, the mobile station has not registered, it is then deregistered.
When a mobile station is powered off, it performs an IMSI detach procedure in order to tell the network that it is no longer connected.
Authentication and security
The authentication procedure involves the SIM card and the Authentication Center. A secret key, stored in the SIM card and the AuC, and a ciphering algorithm called A3 are used in order to verify the authenticity of the user. The mobile station and the AuC compute a SRES using the secret key, the algorithm A3 and a random number generated by the AuC. If the two computed SRES are the same, the subscriber is authenticated. The different services to which the subscriber has access are also checked.
Another security procedure is to check the equipment identity. If the IMEI number of the mobile is authorized in the EIR, the mobile station is allowed to connect the network.
In order to assure user confidentiality, the user is registered with a Temporary Mobile Subscriber Identity (TMSI) after its first location update procedure.
Enciphering is another option to guarantee a very strong security but this procedure is going to be described in section 5.
Communication Management (CM)
The CM function is responsible for:
Call control.
Supplementary Services management.
Short Message Services management.
Call Control (CC)
The CC is responsible for call establishing, maintaining and releasing as well as for selecting the type of service. One of the most important functions of the CC is the call routing. In order to reach a mobile subscriber, a user dials the Mobile Subscriber ISDN (MSISDN) number which includes:
a country code
a national destination code identifying the subscriber’s operator
a code corresponding to the subscriber’s HLR
The call is then passed to the GMSC (if the call is originated from a fixed network) which knows the HLR corresponding to a certain MISDN number. The GMSC asks the HLR for information helping to the call routing. The HLR requests this information from the subscriber’s current VLR. This VLR allocates temporarily a Mobile Station Roaming Number (MSRN) for the call. The MSRN number is the information returned by the HLR to the GMSC. Thanks to the MSRN number, the call is routed to subscriber’s current MSC/VLR. In the subscriber’s current LA, the mobile is paged.
Supplementary Services management
The mobile station and the HLR are the only components of the GSM network involved with this function.
Short Message Services management
In order to support these services, a GSM network is in contact with a Short Message Service Center through the two following interfaces:
The SMS-GMSC for Mobile Terminating Short Messages (SMS-MT/PP). It has the same role as the GMSC.
The SMS-IWMSC for Mobile Originating Short Messages (SMS-MO/PP).
Operation, Administration and Maintenance (OAM)
The OAM function allows the operator to monitor and control the system as well as to modify the configuration of the elements of the system. Not only the OSS is part of the OAM, also the BSS and NSS participate in its functions as it is shown in the following examples:
The components of the BSS and NSS provide the operator with all the information it needs. This information is then passed to the OSS which is in charge of analyzing it and control the network.
The self test tasks, usually incorporated in the components of the BSS and NSS, also contribute to the OAM functions.
The BSC, in charge of controlling several BTSs, is another example of an OAM function performed outside the OSS.
Radio interface
Most of the GSM networks operate at frequency of 900MHz and/or 1800MHz except in USA and Canada where the GSM networks operate at 850/1900 MHz.
The International Telecommunication Union (ITU), which manages the international allocation of radio spectrum, has allocated the bands 890-915 MHz for the uplink (mobile station to base station) and 935-960 MHz for the downlink (base station to mobile station) for mobile networks in Europe. Since this range was already being used in the early 1980s by the analog systems of the day, the CEPT had the foresight to reserve the top 10 MHz of each band for the GSM network that was still being developed. Eventually, GSM will be allocated the entire 2×25 MHz bandwidth.
Multiple access and channel structure
Since radio spectrum is a limited resource shared by all users, a method must be devised to divide up the bandwidth among as many users as possible. The method chosen by GSM is a combination of Time- and Frequency-Division Multiple Access (TDMA/FDMA). The FDMA part involves the division by frequency of the (maximum) 25 MHz bandwidth into 124 carrier frequencies spaced 200 kHz apart. One or more carrier frequencies are assigned to each base station. Each of these carrier frequencies is then divided in time, using a TDMA scheme. The fundamental unit of time in this TDMA scheme is called a “burst period†and it lasts 15/26 ms (or approx. 0.577 ms). Eight burst periods are grouped into a “TDMA frame†(120/26 ms, or approx. 4.615 ms), which forms the basic unit for the definition of logical channels. One physical channel is one burst period per TDMA frame.
Channels are defined by the number and position of their corresponding burst periods. All these definitions are cyclic, and the entire pattern repeats approximately every 3 hours. Channels can be divided into “dedicated channelsâ€, which are allocated to a mobile station, and “common channelsâ€, which are used by mobile stations in idle mode.
Traffic channels
A traffic channel (TCH) is used to carry speech and data traffic. Traffic channels are defined using a 26-frame multiframe, or group of 26 TDMA frames. The length of a 26-frame multiframe is 120 ms, which is how the length of a burst period is defined (120 ms divided by 26 frames divided by 8 burst periods per frame). Out of the 26 frames, 24 are used for traffic, 1 is used for the Slow Associated Control Channel (SACCH) and 1 is currently unused. TCHs for the uplink and downlink are separated in time by 3 burst periods, so that the mobile station does not have to transmit and receive simultaneously, thus simplifying the electronics.
In addition to these “full-rate†TCHs, there are also “half-rate†TCHs defined, although they are not yet implemented. Half-rate TCHs will effectively double the capacity of a system once half-rate speech coders are specified (i.e., speech coding at around 7 kbps, instead of 13 kbps). Eighth-rate TCHs are also specified, and are used for signaling. In the recommendations, they are called Stand-alone Dedicated Control Channels (SDCCH).
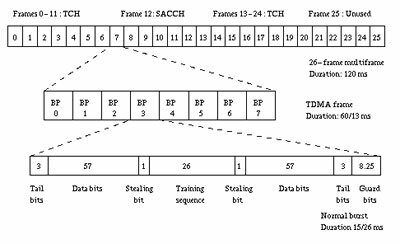
Figure 2: Organization of bursts, TDMA frames, and multiframes for speech and data
Control channels
Common channels can be accessed both by idle mode and dedicated mode mobiles. The common channels are used by idle mode mobiles to exchange the signaling information required to change to dedicated mode. Mobiles already in dedicated mode monitor the surrounding base stations for handover and other information. The common channels are defined within a 51-frame multiframe, so that dedicated mobiles using the 26-frame multiframe TCH structure can still monitor control channels. The common channels include:
Broadcast Control Channel (BCCH): Continually broadcasts, on the downlink, information including base station identity, frequency allocations, and frequency-hopping sequences.
Frequency Correction Channel (FCCH) and Synchronization Channel (SCH): Used to synchronize the mobile to the time slot structure of a cell by defining the boundaries of burst periods, and the time slot numbering. Every cell in a GSM network broadcasts exactly one FCCH and one SCH, which are by definition on time slot number 0 (within a TDMA frame).
Random Access Channel (RACH): Slotted Aloha channel used by the mobile to request access to the network.
Paging Channel (PCH): Used to alert the mobile station of an incoming call.
Access Grant Channel (AGCH): Used to allocate an SDCCH to a mobile for signaling (in order to obtain a dedicated channel), following a request on the RACH.
Burst structure
There are four different types of bursts used for transmission in GSM. The normal burst is used to carry data and most signaling. It has a total length of 156.25 bits, made up of two 57 bit information bits, a 26 bit training sequence used for equalization, 1 stealing bit for each information block (used for FACCH), 3 tail bits at each end, and an 8.25 bit guard sequence, as shown in Figure 2. The 156.25 bits are transmitted in 0.577 ms, giving a gross bit rate of 270.833 kbps.
The F burst, used on the FCCH, and the S burst, used on the SCH, have the same length as a normal burst, but a different internal structure, which differentiates them from normal bursts (thus allowing synchronization). The access burst is shorter than the normal burst, and is used only on the RACH. ‘
Speech coding
GSM is a digital system, so speech signals, inherently analog, have to be digitized. The method employed by ISDN, and by current telephone systems for multiplexing voice lines over high speed trunks and optical fiber lines, is Pulse Coded Modulation (PCM). The output stream from PCM is 64 kbps, too high a rate to be feasible over a radio link. The 64 kbps signal contains much redundancy, although it is simple to implement. The GSM group studied several voice coding algorithms on the basis of subjective speech quality and complexity (which is related to cost, processing delay, and power consumption once implemented) before arriving at the choice of a Regular Pulse Excited – Linear Predictive Coder (RPELPC) with a Long Term Predictor loop. Basically, information from previous samples, which does not change very quickly, is used to predict the current sample. The coefficients of the linear combination of the previous samples, plus an encoded form of the residual, the difference between the predicted and actual sample, represent the signal. Speech is divided into 20 millisecond samples, each of which is encoded as 260 bits, giving a total bit rate of 13 kbps.
 GSM services
It is important to note that all the GSM services were not introduced since the appearance of GSM but they have been introduced in a regular way. The GSM Memorandum of Understanding (MoU) defined four classes for the introduction of the different GSM services:
E1: introduced at the start of the service.
E2: introduced at the end of 1991.
Eh: introduced on availability of half-rate channels.
A: these services are optional.
Three categories of services can be distinguished:
Teleservices.
Bearer services.
Supplementary Services.
Teleservices
Telephony (E1 Eh).
Facsimile group 3 (E1).
Emergency calls (E1 Eh).
Tele-text
Short Message Services (E1, E2, A). Using these services, a message of a maximum of 160 alphanumeric characters can be sent to or from a mobile station. If the mobile is powered off, the message is stored. With the SMS Cell Broadcast (SMS-CB), a message of a maximum of 93 characters can be broadcast to all mobiles in a certain geographical area.
Fax mail. Thanks to this service, the subscriber can receive fax messages at any fax machine.
Voice mail. This service corresponds to an answering machine.
Bearer services
A bearer service is used for transporting user data. Some of the bearer services are listed below:
Asynchronous and synchronous data, 300-9600 bps (E1).
Alternate speech and data, 300-9600 bps (E1).
Asynchronous PAD (packet-switched, packet assembler/disassembler) access, 300-9600 ps (E1).
Synchronous dedicated packet data access, 2400-9600 bps (E2).
Supplementary Services
Call Forwarding (E1). The subscriber can forward incoming calls to another number if the called mobile is busy (CFB), unreachable (CFNRc) or if there is no reply (CFNRy). Call forwarding can also be applied unconditionally (CFU).
Barring of All Outgoing Calls, BAOC (E1).
Barring of Outgoing International Calls, BOIC (E1).
Barring of Outgoing International Calls except those directed toward the Home PLMN Country, BOIC-exHC (E1).
Barring of All Incoming Calls, BAIC (E1)
Barring of incoming calls when roaming (A).
Call hold (E2): Puts an active call on hold.
Call Waiting, CW (E2): Informs the user, during a conversation, about another incoming call. The user can answer, reject or ignore this incoming call.
Advice of Charge, AoC (E2): Provides the user with online charge information.
Multiparty service (E2): Possibility of establishing a multiparty conversation.
Closed User Group, CUG (A): It corresponds to a group of users with limited possibilities of calling (only the people of the group and certain numbers).
Calling Line Identification Presentation, CLIP (A): It supplies the called user with the ISDN of the calling user.
Calling Line Identification Restriction, CLIR (A): It enables the calling user to restrict the presentation.
Connected Line identification Presentation, CoLP (A): It supplies the calling user with the directory number he gets if his call is forwarded.
Connected Line identification Restriction, CoLR (A): It enables the called user to restrict the presentation.
Operator determined barring (A): Restriction of different services and call types by the operator.
Conclusion
The GSM community undertook a big task to provide a uniform standard so that interoperability exists among different users and manufactures resulting in reduced cost and increased quality. The GSM committee has been able to achieve this with success. In today’s world people carry just one communication device for all their purpose irrespective of the national boundaries they are traveling through.
The GSM system operating at 1.8 GHz and 1.9 GHz are a first approach at a true personal communication system. GSM is being used as a basis for the next generation of mobile communication technology in Europe, the Universal Mobile Telecommunication System (UMTS).
4 Responses to “GSM Technology”
kuchh samjhme nahi aaya
By Sujit on Apr 10, 2007
It good men
By Peter on Mar 3, 2011
can you explain in hindi about GSM.
By ajaysingh on Jul 15, 2011
I love this writeup at least i now know the history of GSM.
By Phone Tricks on Mar 6, 2012